Unauthorized file read in mangadex-downloader (CVE-2022-36082)

Impact
Imagine, you want to download manga in a batch file uploaded somewhere in the internet, let's say pastebin (https://pastebin.com/raw/URR2sXV0).
https://mangadex.org/title/77fd8118-61b0-4b1f-95a6-2b839d754f81/tensei-shitara-ken-deshita
https://mangadex.org/title/5a90308a-8b12-4a4d-9c6d-2487028fe319/uzaki-chan-wa-asobitai
https://mangadex.org/title/d7037b2a-874a-4360-8a7b-07f2899152fd/mairimashita-iruma-kun
And some hacker modify your uploaded file and added some url pointed at your computer files that contain sensitive informations. So the original content that contains URLs pointed at MangaDex, is now become this:
/etc/passwd
Then you proceed to download from that batch file that has been modified by the hacker and you get error like this
$ mangadex-downloader "file:https://pastebin.com/raw/URR2sXV0"
[ERROR] "{some sensitive info from /etc/passwd}" is not valid MangaDex URL
You might be confused and say
What happened ? I did put the urls correctly and what is this {some sensitive info} appeared on my console ? I didn't remember putting that on my batch file
Congratulations, your sensitive informations have been appeared in the console.
That was part of security vulnerability (CVE-2022-36082) in mangadex-downloader.
Breakdown
Affected versions:
- 1.3.0
- 1.4.0
- 1.5.0
- 1.6.0
- 1.6.1
- 1.6.2
- 1.7.0
- 1.7.1
Basically, the app was trying to read whole content from a file that has been uploaded to internet. And if that content is exist-as-a-file in user computer, the app will try to open and read the whole content from that file.
The fatal flaw comes from this function
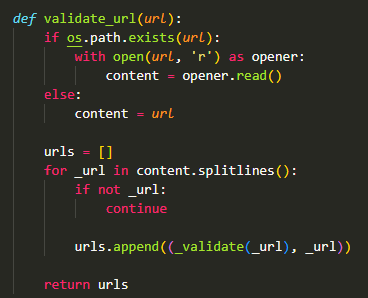
And this
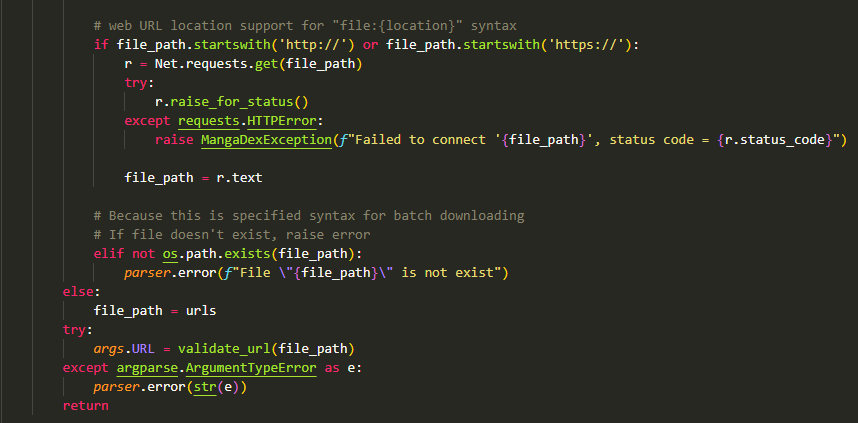
As you can see in "Code snippet 2", the app is try to fetch contents from online file. If success, it will call function validate_url() with file_path argument (See "Code snippet 1"). If value file_path is exist-as-a-file in victim computer, it will try to open and read the contents and proceed to validate url for each lines.
And if the url is not passed the validation, the app will throw an error telling the user
[ERROR] {url} is not valid MangaDex URL
That {url} from online file is exposed to victim console. Which is vulnerable to CWE-200.
Note
The contents file must be single line, it doesn't work if the file contains multiple lines. For example:
This will work
some_super_secret_information.txt
Python POV
if os.path.exists("some_super_secret_information.txt"):
# Do open and read stuff here
This will NOT work
some_super_secret_information.txt
https://mangadex.org/title/d7037b2a-874a-4360-8a7b-07f2899152fd/mairimashita-iruma-kun
https://mangadex.org/title/77fd8118-61b0-4b1f-95a6-2b839d754f81/tensei-shitara-ken-deshita
Python POV
if os.path.exists("some_super_secret_information.txt\nhttps://mangadex.org/title/d7037b2a-874a-4360-8a7b-07f2899152fd/mairimashita-iruma-kun\nhttps://mangadex.org/title/77fd8118-61b0-4b1f-95a6-2b839d754f81/tensei-shitara-ken-deshita"):
# The file will not be read
# Because it's not exist in victim computer
So who is to blame for ?
Me actually ?. I was working on v2.0.0 and refactoring some code that is total mess and i found this function can be exploited. I forgot to change how function validate_url() work since v1.3.0 is released and thus CVE-2022-36082 is born.
From my deepest heart, i apologies.
Solution
Install latest version of mangadex-downloader ( >= v1.7.2 ) or if you're too lazy to update, make sure to double check the url that it's safe to download.